AWS Network Firewall
What is the Network Firewall
As AWS describes it:
AWS Network Firewall is a managed service that makes it easy to deploy essential network protections for all of your Amazon Virtual Private Clouds (VPCs). The service can be set up with just a few clicks and scales automatically with your network traffic so you don’t have to worry about deploying and managing any infrastructure. Network Firewall’s flexible rules engine lets you define firewall rules that give you fine-grained control over network traffic, such as blocking outbound Server Message Block (SMB) requests to prevent the spread of malicious activity. You can also import rules you’ve already written in common open source rule formats or import compatible rules sourced from AWS partners. AWS Network Firewall works together with AWS Firewall Manager so you can build policies based on AWS Network Firewall rules and then centrally apply those policies across your VPCs and accounts.
The general gist behind the customer case was to meet security requirements from a new client they had. All traffic had to be routed through the firewall.
General Setup
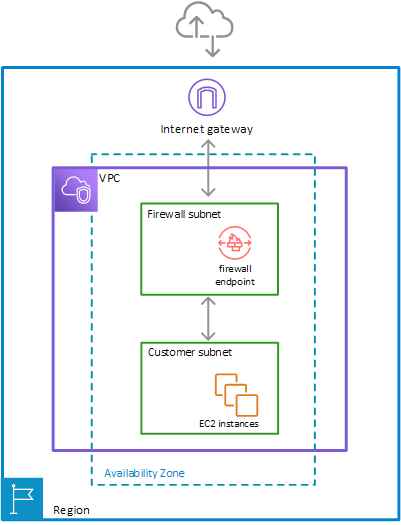
With these steps as listed by the AWS docs: To install and use an AWS Network Firewall firewall in your Amazon Virtual Private Cloud VPC, you configure the firewall components and your VPC’s subnets and route tables in the following high-level steps.
-
Configure the VPC subnets for your firewall endpoints – In your VPC, in each Availability Zone where you want a firewall endpoint, create a subnet specifically for use by Network Firewall. A firewall endpoint can’t protect applications that run in the same subnet, so reserve these subnets for exclusive use by the firewall. The subnets that you use for your firewall endpoints must belong to a single AWS Region and must be in different Availability Zones within the Region. Network Firewall is available in the Regions listed at AWS service endpoints.
-
Create the firewall – Create a Network Firewall firewall and provide it with the specifications for each of your firewall subnets. Network Firewall creates a firewall endpoint in each subnet that you specify, available to monitor and protect the resources for the subnets whose traffic you send through it.
-
Configure the firewall policy – Define the firewall policy for your firewall by specifying its rule groups and other behavior that you want the firewall to provide.
-
Modify your VPC route tables to include the firewall – Using Amazon VPC ingress routing enhancements, change your routing tables to route traffic through the Network Firewall firewall. These changes must insert the firewall between the subnets that you want to protect and outside locations. The exact routing that you need to do depends on your architecture and its components.
Keep in mind
Traffic has to flow symmetrical meaning that the flow of data had to go through the same VPC Endpoint.
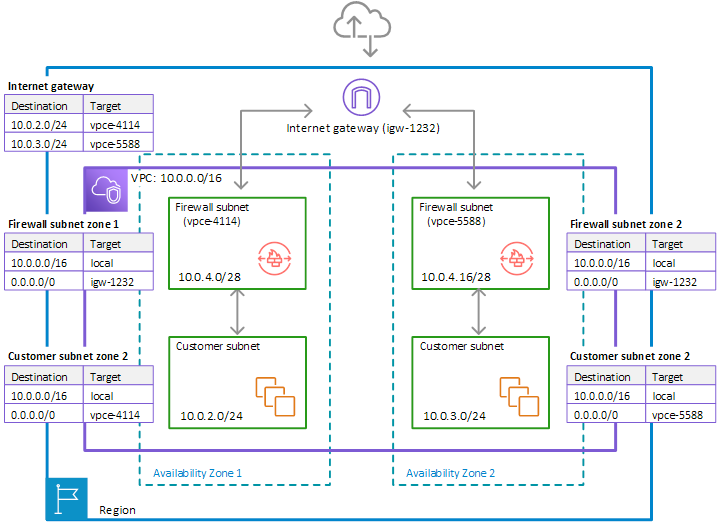
Now here is the thing: Usually you have multiple AZ’s and the same amount of subnets. When you are using Terraform and and eg the VPC module, these module will create 1 single RouteTable that is attached to all 3 (public | private |data )subnets.
Take a look at this picture of a 2 AZ setup with just 1 type of subnet to keep it simple. In this case the Terraform module would have attached 1 RT to 10.0.2.0/24 and 10.0.3/24. But remember about the symmetrical flow. So one of the issues is that with the VPC module of Terraform this behavior can not be changed.
You have to have N route tables, one for each subnet. In this route able you have to add the VPC endpoint that is part of the created firewall subnet.
Tip for Dev environment
There is nothing stopping you from using a single firewall subnet and thus a single VPC endpoint for all you subnets. You are sacrifice fault tolerance and if that is an acceptable risks it might be a good way to make it less complex and also safe quite some money. The firewall VPC endpoint are particularly expensive. A 3 VPCe setup runs well into $60 a day (traffic not included).
To be continued..